Network Access Requests
Optimize network access requests with automation to efficiently manage connectivity.
Why automate?
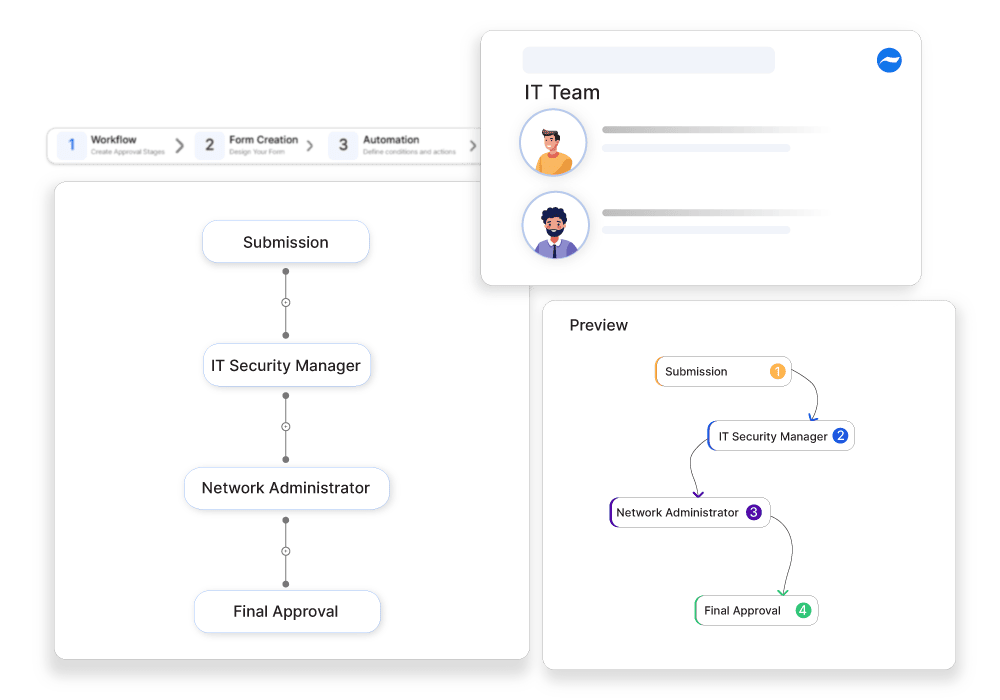
Employees initiate network access requests when they need to access or modify an organization’s network resources such as databases, applications, and even servers. The process is critical as it is related to the company’s network security. It needs to be optimized to ensure all the employees, partners, and contractors comply with the company standard when performing their roles related to maintaining network security.
Without a structured approach to managing these requests, there can be unauthorized access, data breaches, and compliance issues. Automating these requests streamlines the approval process where the requests are verified precisely, and get necessary approvals and access controls. Automating this process gives better control over network security reducing security breaches and enhancing compliance.
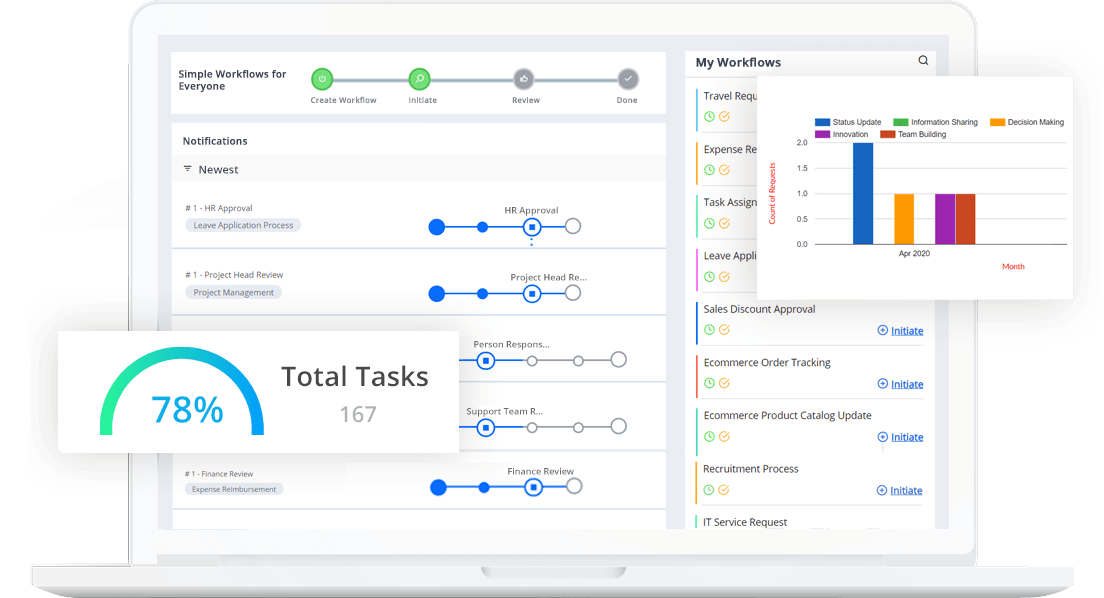
How Cflow Can Help Automate the Process
Centralized Access Request Submission
Cflow offers a centralized platform for extracting and storing all necessary information from the requests thereby simplifying the approval process and ensuring data consistency. details such as the purpose of access and required resources. This centralization simplifies the request process and ensures that all necessary information is collected.
Automated Approval Routing
Cflow automates approval routing to ensure that requests reach the relevant approvers on time based on predefined criteria ensuring that the access is granted only after thorough review and approval maintaining network security.
Secure Access Provisioning
Cflow offers secured access provisioning by seamlessly integrating with network management systems. This automates the access provisioning process and reduces the approval time for granting permissions to prevent unauthorized access.
Comprehensive Audit and Monitoring
Cflow offers a comprehensive audit trail that includes detailed information on the requests and approvals helping organizations to monitor access permissions, maintain compliance, and quickly identify risks and address any unauthorized access attempts.
Transform & streamline business processes with cloud BPM & workflow automation software.
Join 100k + Users Who Are Already Using Cflow
“I’m really impressed with the support provided by Cflow. There has never been a time when they have kept me waiting. A product that is simple to use and a team that is smart and extremely fast are factors that help me feel reassured and confident.”

Ronald Tibay
Senior IT Manager @ NutriAsia, Inc
“The WFH environment during the COVID-19 pandemic made it clear how inefficient our processes were. Cflow allowed us to digitize paper forms with automated workflows. If you can envision a tool for an online workflow, it can be done in Cflow!”

Stephanie Duncan
Registrar @ Freed-Hardeman University
“We are extremely liking CFlow. So far any issues that we’ve had once we contacted support they were able to help us resolve the issue. This has helped us take a paper process and replace it, faster and more streamlined now for us.”

Bradley Wilkins
Director of Technology @Hazel Park School